About BMU
Bhagwan Mahavir University, run by BHAGWAN MAHAVIR EDUCATION FOUNDATION is committed to inclusion and innovation in education through philanthropy and pioneering initiatives. Bhagwan Mahavir University provides world class education and empowering opportunities for all sections of society. As the world of business and job opportunities are changing rapidly, we are evolving to make our students not just job ready but also life ready, to help them see learning as a continuous process and to become future- ready professionals.
Latest Circular
- 2023-10-27
Surat Startup & Innovation Conclave
- 2023-07-06
BMU CAREER EXPO 2023
- 2023-06-17
Surya Namashkar
- 2023-05-01
Digital Detox Policy-BMU
- 2023-04-27
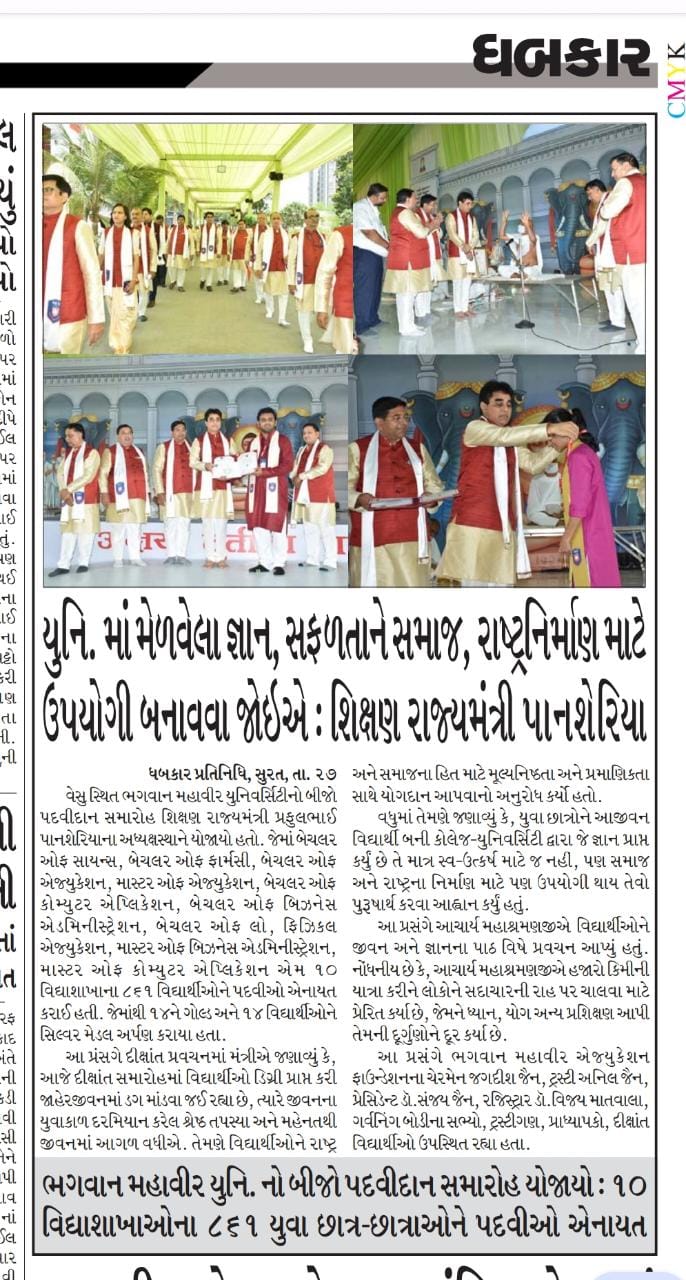
2nd Convocation of Bhagwan Mahavir University
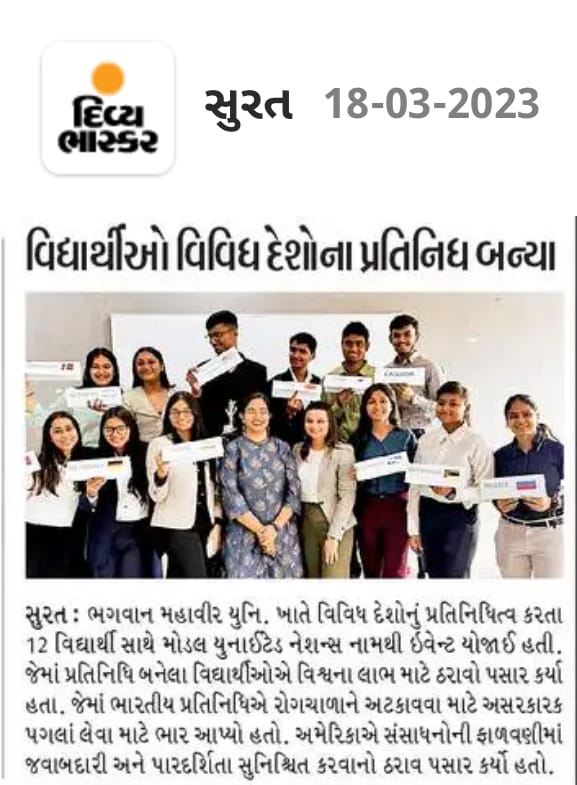
- 2023-03-23
Annual Function (SPANDAN-Connecting heart beat)-2023
Master in Technology In Real Estate Valuation & Master of Technology in Plant and Machinery Valuation
Our Highlights

We are an AICTE recognized and UGC-affiliated university, further processing for NAAC accreditation.

We have a wide range of facilities that are open to students, staff, visitors, and the local community. We are proud of our welcoming and friendly home of learning.

We provide comprehensive support to students with the optimal progression of their skills during these pandemic times.
Media & Press

Sahil Arora
BMBBA, Batch -2011-13

Vinita Singh
MSCET - Computer, 2016 passout